Introduction
MouseJack is a class of vulnerabilities that affects the vast majority of wireless, non-Bluetooth keyboards and mice. This tutorial requires to have the Crazyradio PA USB device.
Using the crazyradio is very easy and we are still impressed that we found a vulnerable keyboard while doing this tutorial!
Step 1: Install requirements
sudo apt-get install sdcc binutils python python-pip git
sudo pip install -U pip
sudo pip install -U -I pyusb
sudo pip install -U platformio
Step 2: Download source code
git clone https://github.com/BastilleResearch/mousejack.git
git submodule init
git submodule update
Then we need to make the firmware for crazyradio and flash over USB:
cd nrf-research-firmware
make
sudo make install
Step 3: Using scanner and sniffer
Once your crazyradio device has the new firmware you are ready to use your device. Inside the mousejack directory you can find nrf-research-firmware/tools subdirectory with contains the scripts nrf24-scanner.py and nrf24-sniffer.py.
Here as example of usage:
sudo ./nrf24-scanner.py -l -v
You will see the following output if everything is working ok:
[2018-09-22 19:36:56.043] Using channels 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, 24, 25, 26, 27, 28, 29, 30, 31, 32, 33, 34, 35, 36, 37, 38, 39, 40, 41, 42, 43, 44, 45, 46, 47, 48, 49, 50, 51, 52, 53, 54, 55, 56, 57, 58, 59, 60, 61, 62, 63, 64, 65, 66, 67, 68, 69, 70, 71, 72, 73, 74, 75, 76, 77, 78, 79, 80, 81, 82, 83
[2018-09-22 19:36:56.198] Entered promiscuous mode
[2018-09-22 19:36:56.201] Tuned to 2
[2018-09-22 19:36:56.304] Tuned to 3
[2018-09-22 19:36:56.407] Tuned to 4
[2018-09-22 19:36:56.510] Tuned to 5
[2018-09-22 19:36:56.613] Tuned to 6
````
Then to sniff use the nrf24-sniffer.py -a with the device address.
# Optional step: install jackit
Jackit is a nicer way to show a list of devices. You can install it with the following steps:
```bash
git clone https://github.com/insecurityofthings/jackit.git
cd jackit
sudo pip install -e .
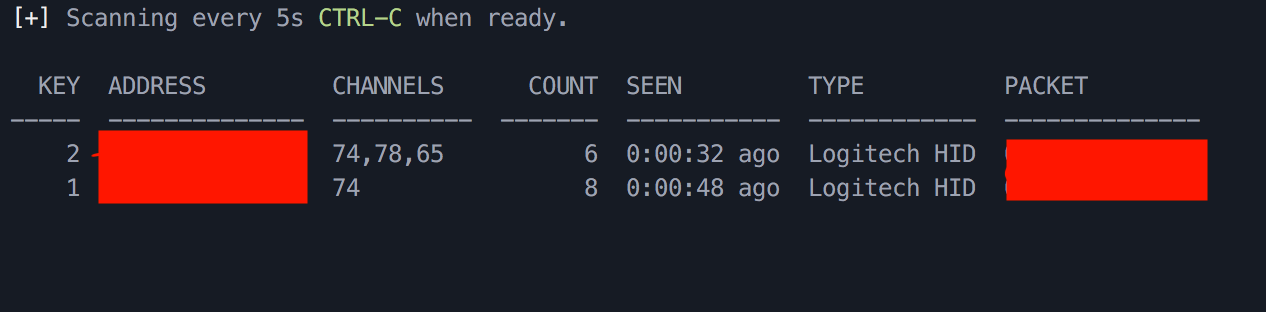
sudo jackit
You will see a list of devices like in this screenshot:
Fixing the vulnerability of your devices
In our case the logitech was vulnerable and to update the firmware we downloaded a tool from logitech website. The tool has a wizard to update each device firmware.